作者:公布时间:2013-02-25阅读次数:15754评论:4
作者:riusksk【TSRC】
博客:http://riusksk.blogbus.com
微博:http://t.qq.com/riusksk
时间:2013年2月12日
前言
2012年10月15日exploit-db漏洞公布站点上发布了《QQPlayer 3.7.892 m2p quartz.dll Heap Pointer Overwrite PoC》,后被人提交至乌云和CNCERT。但经过腾讯安全应急响应团队的分析,确认该漏洞与QQ影音无关,而是微软DirectShow quartz.dll在解析M2P文件时存在堆溢出漏洞,随后腾讯安全团队及时报与微软应急响应中心(MSRC),微软回复确认漏洞存在并于2013/2/12发布补丁修复,其对应的微软编号及CVE编号分别为MS13-011和CVE-2013-0077,具体漏洞公告参见:http://technet.microsoft.com/zh-cn/security/bulletin/ms13-011。
技术分析
Windbg附加QQ影音进程运行后打开poc.m2p,触发异常:
(4c8.6bc): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=41414141 ebx=003f0000 ecx=41414141 edx=03128e40 esi=03128e38 edi=00000012 eip=7c930efe esp=0465f998 ebp=0465fbb8 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 ntdll!RtlAllocateHeap+0x653: 7c930efe 8b39 mov edi,dword ptr [ecx] ds:0023:41414141=????????
开启堆尾检查htc后,重新加载执行后可知这里发生堆溢出:
0:003> g
HEAP[QQPlayer.exe]: Heap block at 030609F0 modified at 03060D48 past requested size of 350
(668.7b8): Break instruction exception - code 80000003 (first chance)
eax=030609f0 ebx=03060d48 ecx=7c93eab5 edx=02a5f842 esi=030609f0 edi=00000350
eip=7c92120e esp=02a5fa44 ebp=02a5fa48 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!DbgBreakPoint:
7c92120e cc int 3
0:003> !heap -p -a 030609F0
address 030609f0 found in
_HEAP @ 3f0000
HEAP_ENTRY Size Prev Flags UserPtr UserSize - state
030609f0 006d 0000 [07] 030609f8 00350 - (busy)
? quartz+8c18
0:003> dd 03060D48
03060d48 41414141 41414141 41414141 41414141
03060d58 41414141 42414141 41424242 41414141
03060d68 41414141 ab414141 abababab feeefeee
03060d78 00000000 00000000 0005000b 011a042c
03060d88 003f01d0 003f4060 feeefeee feeefeee
03060d98 feeefeee feeefeee feeefeee feeefeee
03060da8 feeefeee feeefeee feeefeee feeefeee
03060db8 feeefeee feeefeee feeefeee feeefeee
0:003> dd 03060D48 -111
03060c37 02ef3800 f700007d 00000004 adf00d00
03060c47 000000ba 00000100 5c28f500 28f5c28f
03060c57 00000000 adf00d00 adf00dba adf00dba
03060c67 adf00dba adf00dba 065d3bba 00000000
03060c77 00041400 00014100 1a400000 adf00d00
03060c87 065d3bba 00000000 bfced900 000eaa41
03060c97 97d96000 0005f301 0007d000 00000000
03060ca7 0000c300 01000000 414141b3 ba414141
0:003> ? 03060D48 - 03060cab
Evaluate expression: 157 = 0000009d
开启页堆hpa后,重新附加运行后,在复制数据到堆边界时断下:
(4b8.358): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=000000c3 ebx=003fac98 ecx=00000003 edx=000000f7 esi=001bbdd4 edi=003fb000 eip=7d0706d0 esp=02a5f650 ebp=02a5f658 iopl=0 nv up ei pl nz na po nc cs=001b ss=0023 ds=0023 es=0023 fs=0038 gs=0000 efl=00010202 quartz!ParseSequenceHeader+0x114: 7d0706d0 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
重新在此处设置断点再附加进行:
0:002> bl 0 e 7d0706d0 0001 (0001) 0:**** quartz!ParseSequenceHeader+0x114
在quartz!ParseSequenceHeader+0x114 :rep movs dword ptr es:[edi],dword ptr [esi] 断下后,发现其正在复制poc.m2p文件中的数据,从b3010000开始的数据:
0:002> dd edi 003f8454 baadf00d baadf00d baadf00d baadf00d 003f8464 baadf00d baadf00d baadf00d baadf00d 003f8474 baadf00d baadf00d baadf00d baadf00d 003f8484 baadf00d baadf00d baadf00d baadf00d 003f8494 baadf00d baadf00d baadf00d baadf00d 003f84a4 baadf00d baadf00d baadf00d baadf00d 003f84b4 baadf00d baadf00d baadf00d baadf00d 003f84c4 baadf00d baadf00d baadf00d baadf00d 0:002> dd esi 001bd3a8 b3010000 41414141 41ba4141 41414141 001bd3b8 41414141 41414141 41414141 41414141 001bd3c8 41414141 41414141 41414141 41414141 001bd3d8 41414141 41414141 41414141 41414141 001bd3e8 41414141 41414141 41414141 41414141 001bd3f8 41414141 41414141 41414141 41414141 001bd408 41414141 41414141 41414141 41414141 001bd418 41414141 41414141 41414141 41414141 0:002> kb ChildEBP RetAddr Args to Child 02a5f658 7d02d5ef 001bd3a8 000000c3 003f8420 quartz!ParseSequenceHeader+0x114 02a5f678 7cf9de4f 001be0c0 003fad38 02a5f6a0 quartz!CMpegVideoCodec::CheckInputType+0x7c 02a5f688 7cf94071 001be0c0 003fad44 03fb4148 quartz!CTransformInputPin::CheckMediaType+0x16 02a5f6a0 03f5d397 003f81fc 00000000 001be0c0 quartz!CBasePin::ReceiveConnection+0x71 WARNING: Stack unwind information not available. Following frames may be wrong. 02a5f6d4 03f5f141 03fb4148 003fad44 00000000 splitter!DllGetClassObject+0x177a 02a5f700 03f5f1f0 00000000 ba5279fe 03060c90 splitter!DllGetClassObject+0x3524 02a5f728 7cf9e038 03fb3d68 003fad44 00000000 splitter!DllGetClassObject+0x35d3 02a5f754 7cfa22bd 03fb4154 003fad44 00000000 quartz!CFilterGraph::ConnectDirectInternal+0x40 02a5f774 005a39b3 03060d2c 03fb4154 003fad44 quartz!CFilterGraph::ConnectDirect+0x6c 02a5f7e4 005a45e1 03060c90 03fb4154 003fad44 QQPlayer!CxIOFile::~CxIOFile+0xa7223 02a5f838 005a28ef 020a9014 03fb4154 003fad44 QQPlayer!CxIOFile::~CxIOFile+0xa7e51 02a5f87c 005a90f6 003fad44 03fb4154 003faf18 QQPlayer!CxIOFile::~CxIOFile+0xa615f 02a5f9d4 005a65fb 010a9014 03fb4154 00000000 QQPlayer!CxIOFile::~CxIOFile+0xac966 02a5fa8c 005aab46 010a9014 03fb3d24 00000000 QQPlayer!CxIOFile::~CxIOFile+0xa9e6b 02a5fb98 00545778 0064df93 0207c2c8 00000000 QQPlayer!CxIOFile::~CxIOFile+0xae3b6 02a5fdb0 005476c7 014bdc68 0000c000 00b11f94 QQPlayer!CxIOFile::~CxIOFile+0x48fe8 02a5fe6c 00530189 014bdc68 00000000 02a5ff68 QQPlayer!CxIOFile::~CxIOFile+0x4af37 02a5fe88 783489df 00000000 014bdc68 00194cb8 QQPlayer!CxIOFile::~CxIOFile+0x339f9
函数调用流程:
quartz!CBasePin::ReceiveConnection =》 quartz!CTransformInputPin::CheckMediaType =》quartz!CTransformInputPin::CheckMediaType =》 quartz!ParseSequenceHeader
在解析”\x00\x00\x01\xb3 “头数据时,程序会将该字段数据(从起始地址001bd3a8到至结束标志”\x00\x00\x01\x00”之间的数据,共0xC3字节)复制到一块已初始化的堆内存上(地址为003f8454),而目标地址edi至堆尾的空间只有157(0x9D)< 0xC3,由于未对复制的数据大小进行检测,导致最后因堆溢出覆盖未分配的堆块上,导致异常。
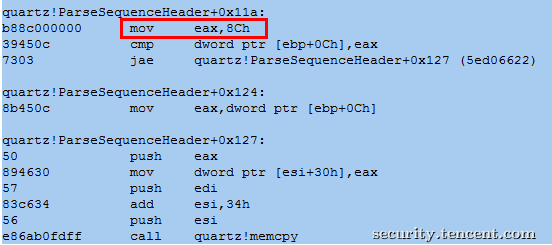
在WIN7系统上的quartz.dll (6.6.7600.16905) 并不存在此漏洞,因为它将数据拷贝的大小限制为0x8C,防止堆溢出,这也是为何poc.m2p只在XP崩溃而在WIN7无法崩溃的原因(如下图),同时该漏洞也影响到Vista和Server 2008等系统,具体受影响的系统请参见微软公告。
可利用性
通过堆溢出覆盖虚表指针可劫持EIP,达到执行任意代码的目的:
(4cc.76c): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=003fa2a4 ebx=030a9d58 ecx=42414141 edx=00000000 esi=030a9d40 edi=003fa298 eip=7cf8a9fa esp=02a7f824 ebp=02a7f838 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=0038 gs=0000 efl=00010246 quartz!CEnumPins::Next+0x9e: 7cf8a9fa ff5104 call dword ptr [ecx+4] ds:0023:42414145=????????
漏洞修复
通过下载官方发布的补丁可修复该漏洞,请广大用户及时更新补丁,补丁下载地址:http://technet.microsoft.com/zh-cn/security/bulletin/ms13-011 。
漏洞响应流程
2012年10月20日——通过邮件将漏洞反馈给微软
2012年10月22日——微软回复邮件并确认漏洞
2013年02月12日——微软发布补丁修复漏洞
捐款成功,感谢您的无私奉献
评论留言